Initial Setup and Next Steps
After completing the technical installation of ABCD, there are crucial configuration steps to perform before using the system in production. These steps ensure security and personalization.
1. Accessing the System
In version 3.1+, the access points have been reorganized:
- Public Access (OPAC):
http://localhost:9090- This is what your library users will see by default.
- Administrative Panel (Central):
http://localhost:9090/admin- This is where librarians and staff log in to manage the system.
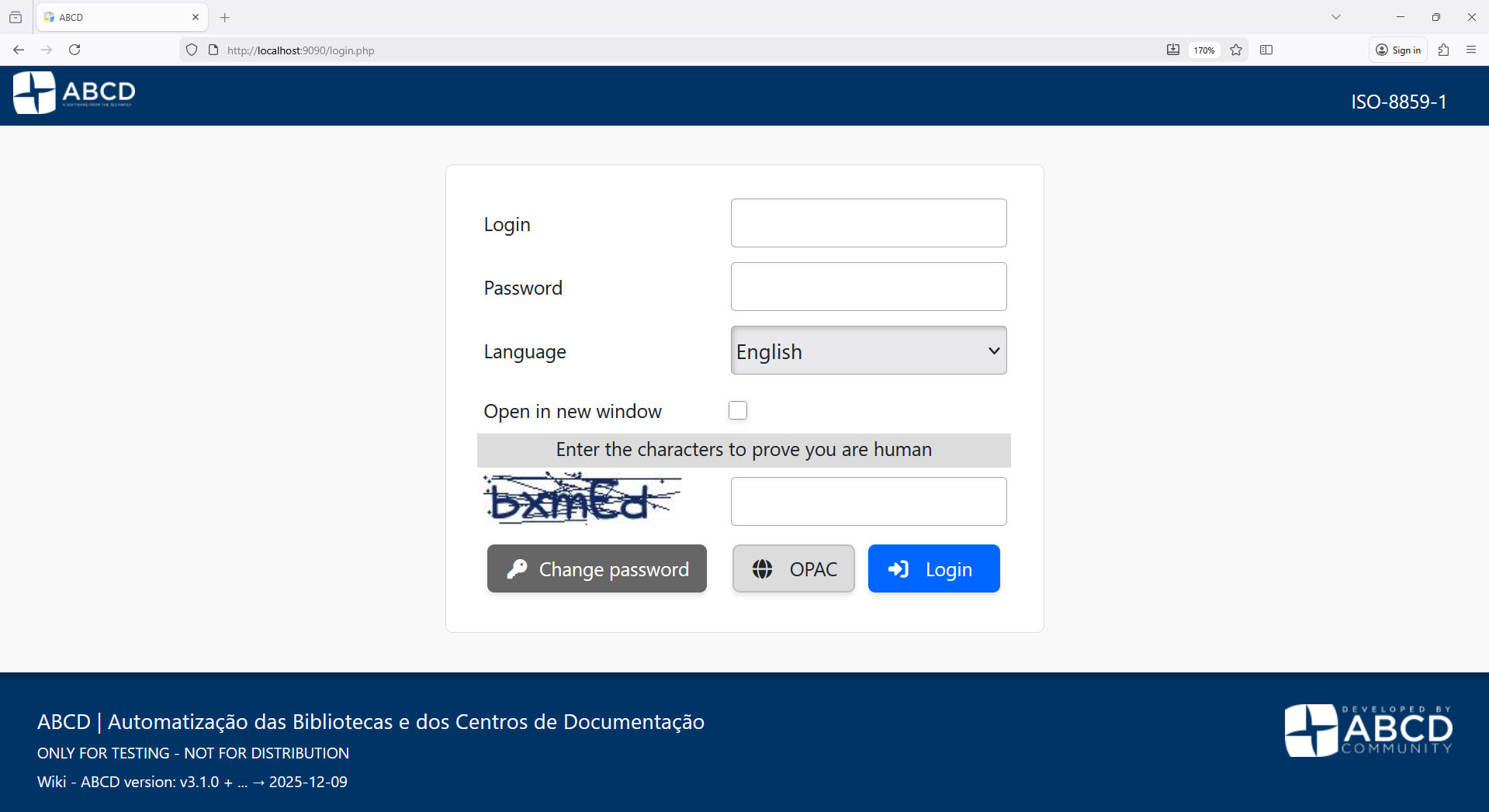 (The new administrative login screen)
(The new administrative login screen)
2. Change Administrator Password (Critical)
The default credentials are public knowledge. Keeping them represents a major security risk.
- Access the Administrative Panel (
/admin). - Log in with the default superuser:
- User:
abcd - Password:
adm
- User:
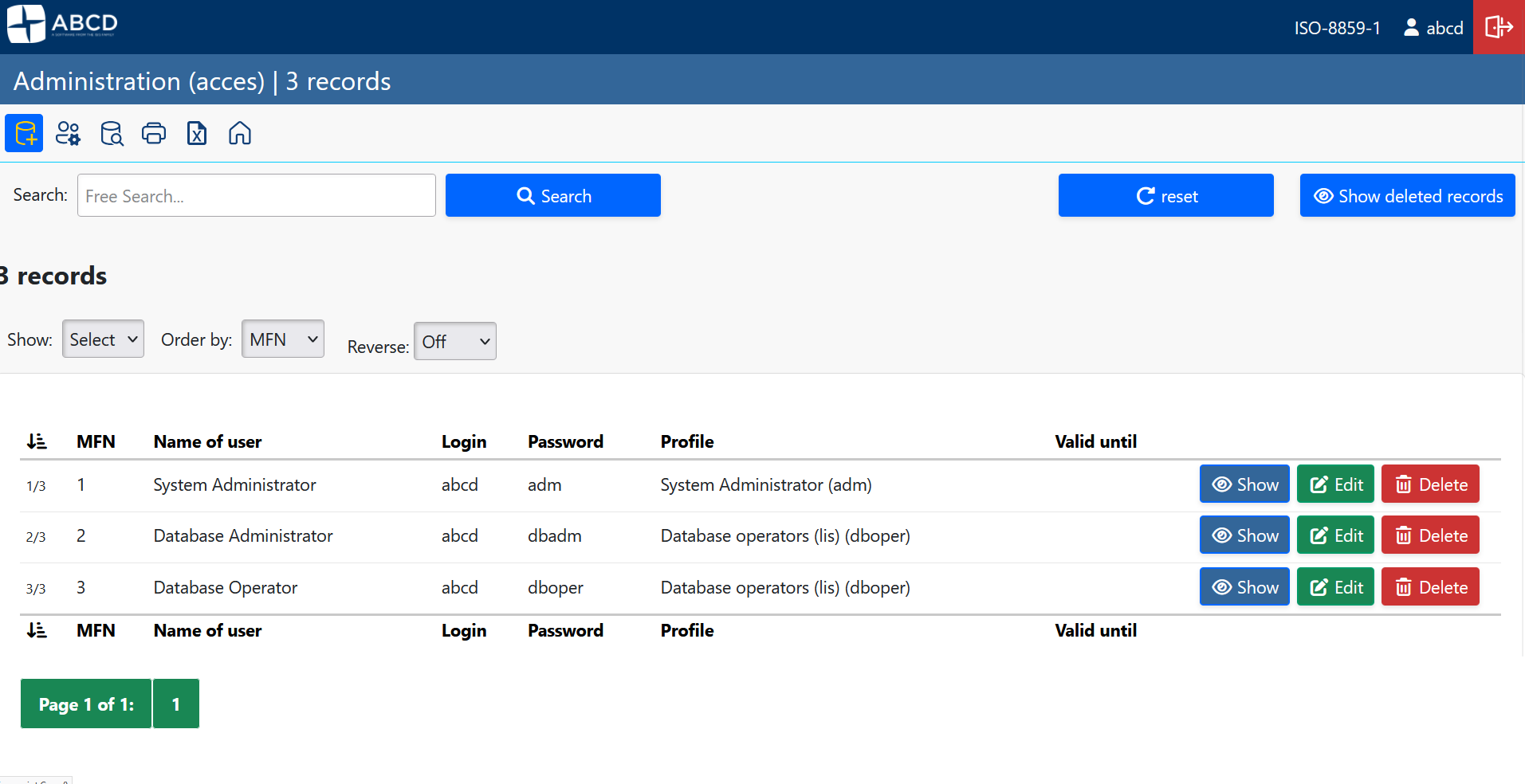
- In the main menu, navigate to Administration > User administration.
- Click on the User administration icon.
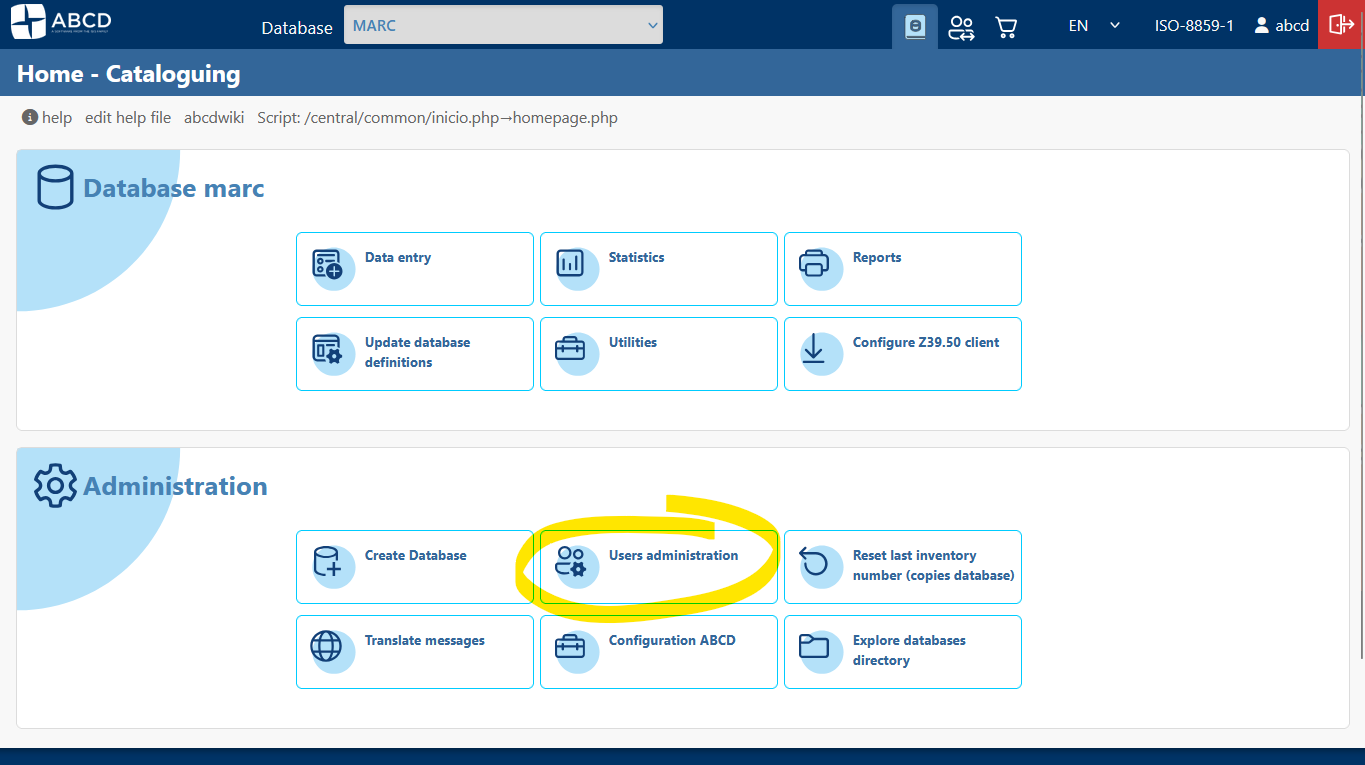
- Locate the operator abcd in the list and click the Edit (pencil) icon.
- Enter a new, strong password in the "Password" and "Confirm password" fields.
- Click Save.
3. Customize Institution Identity
You should replace the generic ABCD logos and texts with your institution's branding.
-
Go to Administration > ABCD Configuration.
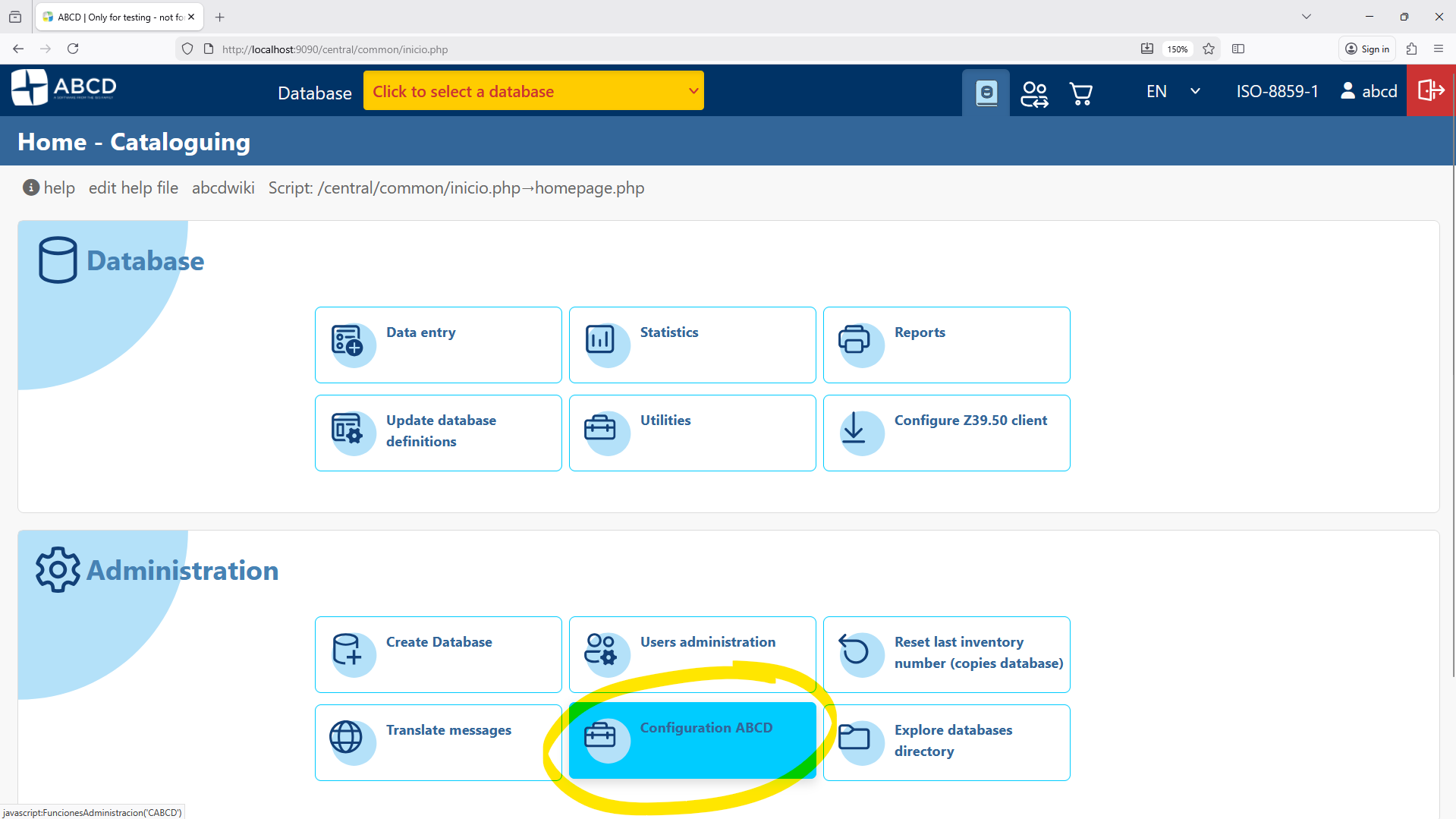
-
Select System settings (abcd.def).
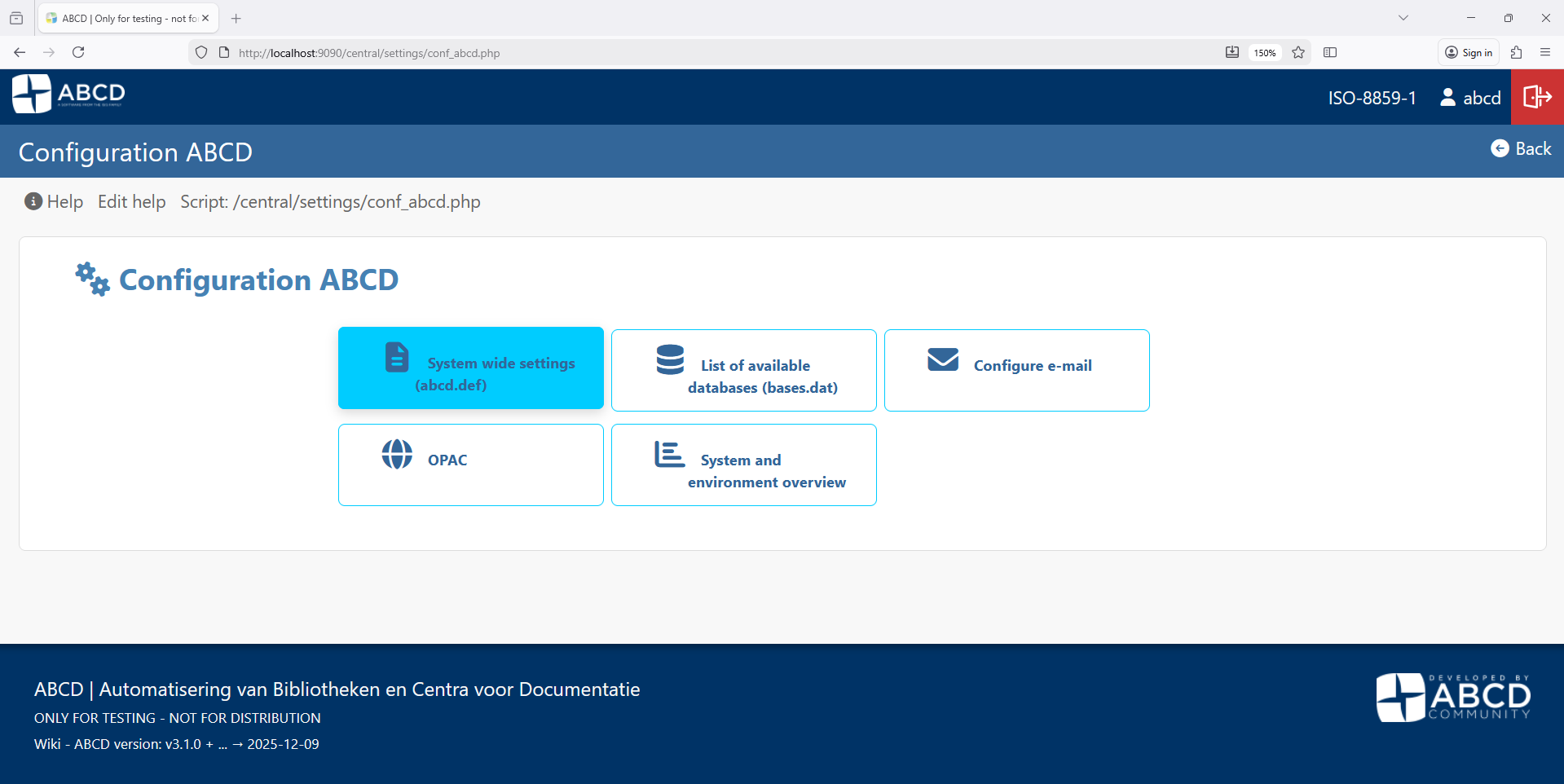
-
Here you can modify:
- Institution Name: Appears in headers and reports.
- Logo: You can upload your library's logo file.
- URL: The official website of your institution.
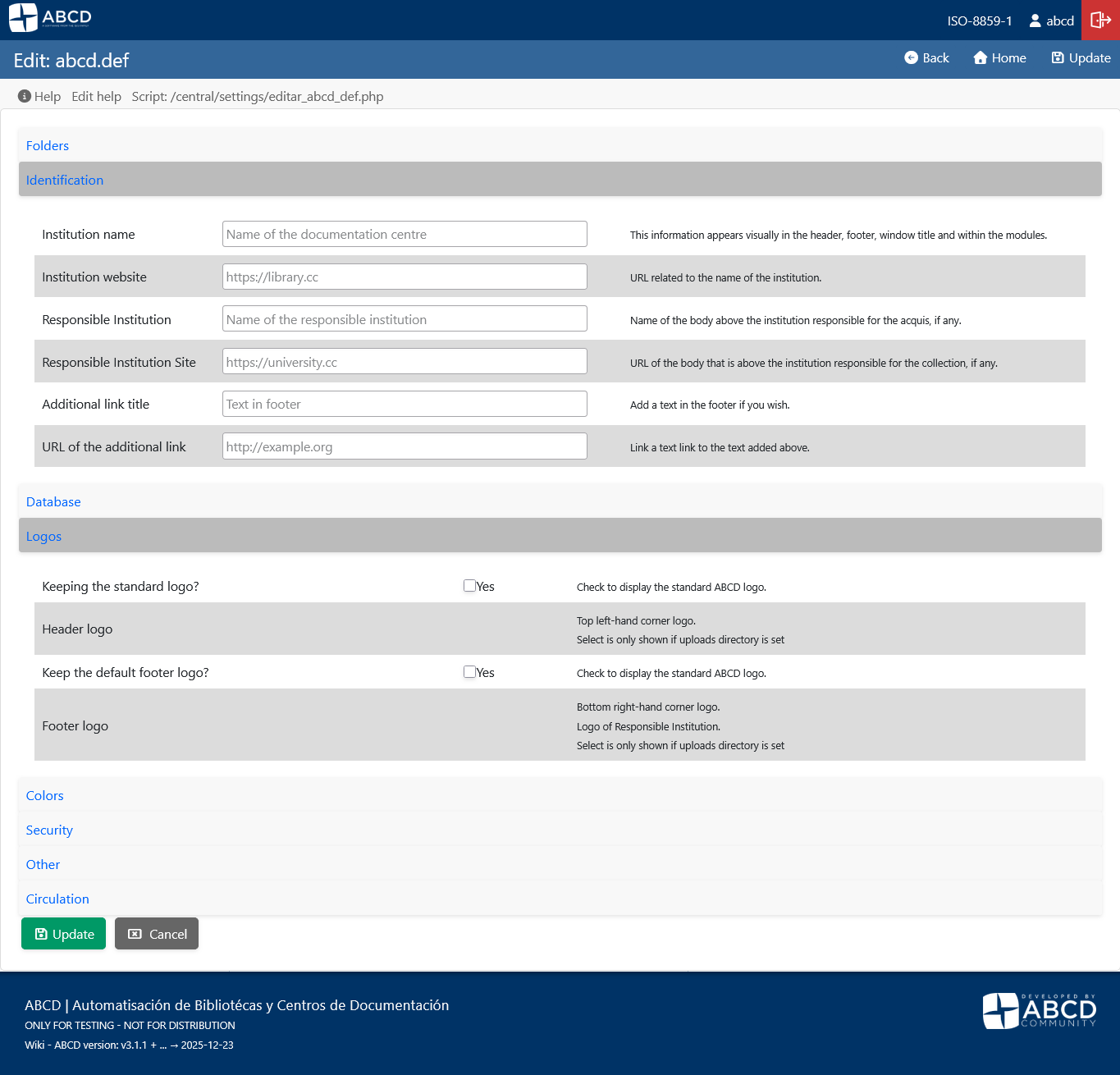
Changes made here reflect immediately on the internal interface. For the OPAC customization, please refer to the OPAC Configuration section in the documentation.
4. Create Profiles and Operators
Avoid using the generic abcd superuser for daily tasks. Create individual accounts for your team.
- Define Profiles:
- Go to User administration > Create/edit profiles.
- Create roles like "Cataloger" (access to Data Entry only) or "Circulation Desk" (Loans only).
- Create Users:
- Go back to User administration.
- Click New user.
- Assign a personalized username, password, and the appropriate Profile.
5. Next Steps
Now that your system is secure and personalized, you are ready to start: